Singularity™ Mobile
device, adaptive, real-time defense.
The Evolving Risks for Mobile Security
Mobile Malware
Mobile devices are top targets for modern threats. From data-stealing apps to ransomware, today’s malware is fast, evasive, and exploits weaknesses.
Mobile Phishing and Smishing
Phishing and smishing exploit everyday mobile habits. Attackers use apps, texts and social media to trick users into clicking malicious links.
BYOD Security
BYOD programs boost productivity, but without proper controls, personal devices can expose corporate data through breaches, leaks, and more.
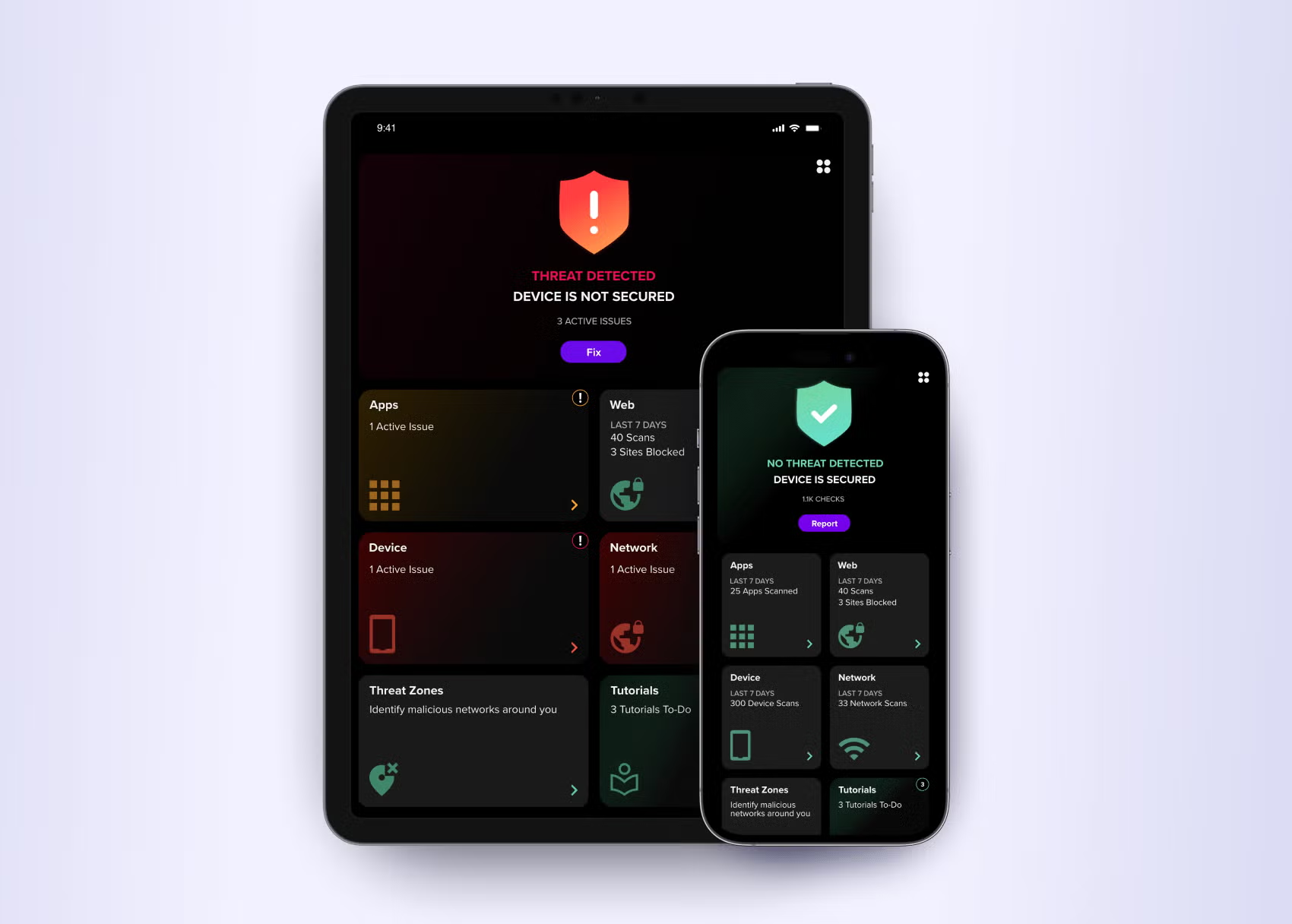
Autonomous AI Protection & Visibility
- Detects and protects against zero-day mobile malware and phishing attacks with powerful behavioral models.
- Eliminates risks from jailbroken and rooted devices.
- Defends against man-in-the-middle (MITM) attacks including rogue wireless and secure communications tampering.
- Stays ahead of tomorrow’s threats with continuous, autonomous learning.

Stop Mobile Phishing Before It Starts
- Block known phishing URLs and behaviorally detect emerging phishing techniques.
- Alert users to suspicious links in texts, messaging apps, email, and social media.
- Prevent credential theft and account compromise before users engage.
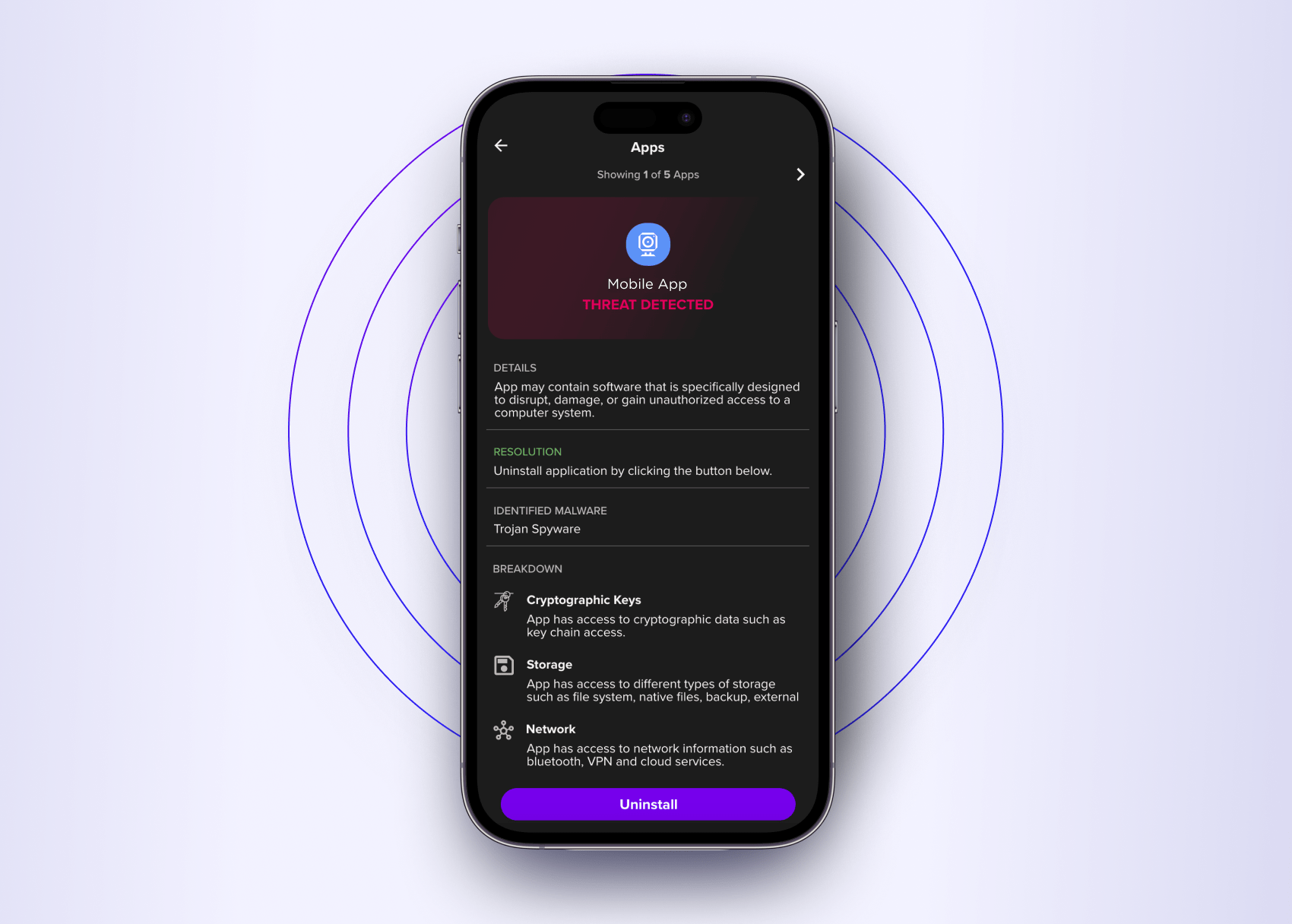
Mobile App
Vetting Built In
- Scan apps on devices to identify security and privacy violations.
- Flag apps with risky permissions or suspicious behavior.
- Allow admins to mark specific apps as non-compliant and restrict access accordingly.
- Automate compliance enforcement via conditional access policies.
- Admins can see which apps are using AI.

Safer Connections
on Any Wifi Network
- Detect and alert users to rogue wifi networks or man-in-the-middle (MITM) attempts.
- Automatically assesses network safety before sensitive data is transmitted.
- Block unsafe communications, or redirect before exposure occurs.
- Ideal for remote users, travelers, and frontline workers in the field.

Privacy First
- Protect personally identifiable information (PII) across devices and media types.
- Maintain user privacy while securing corporate resources.
- Prevent unauthorized access and accidental data exposure on BYOD devices.
Singularity Mobile Secures Devices On The Move
Mobile devices are increasingly relied upon for remote work, authentication, and verification of trust.
Effective & Efficient
AI-powered protection. No cloud required.
Mobile Visibility
Vital device visibility. Vulnerabilities identification.
Privacy by Design
Balances data privacy with security.
MDM Optional
Works with leading MDMs, or without an MDM.
All Major Platforms
iOS, Android, Chrome OS.
Easy to Manage
Zero tough deployment. Maximum protection.
Experience Singularity Endpoint
Ready to see how Singularity Mobile can protect your organization with an AI-powered first line of defense? Connect with a product expert to learn how you can achieve:
- Unparalleled protection, detection, and visibility
- Lightning-fast response and remediation
- Streamlined and more powerful SecOps with
agentic AI
Experience the World’s Most Advanced Cybersecurity Platform
See how our intelligent, autonomous cybersecurity platform harnesses the power of data and AI to protect your organization now and into the future.



